Relevant and actionable intelligence, at scale
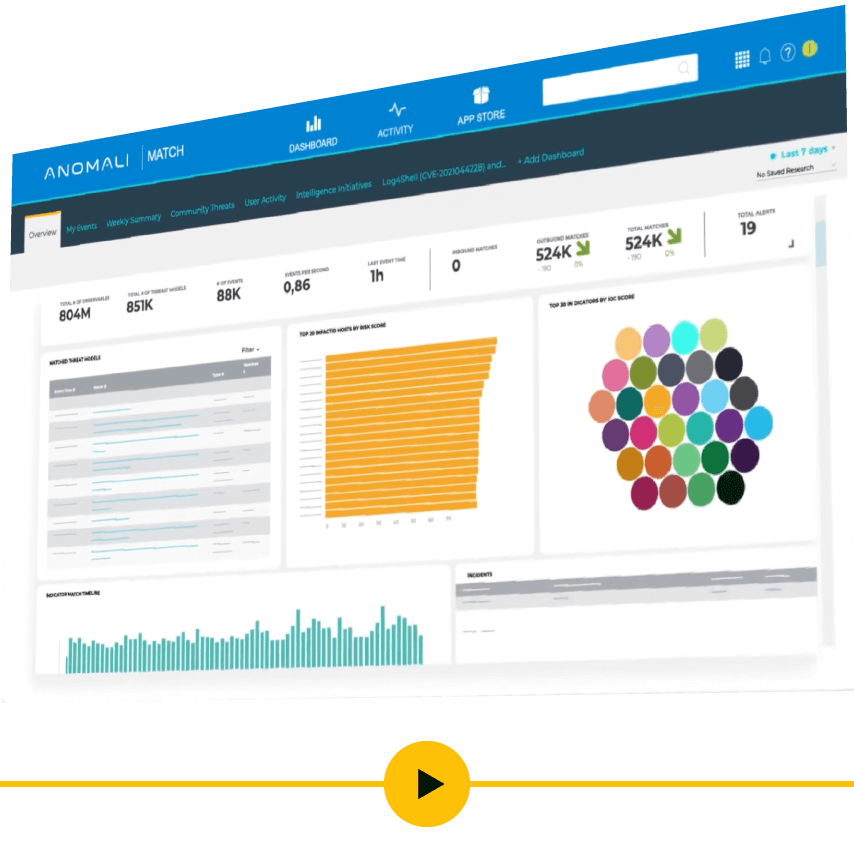
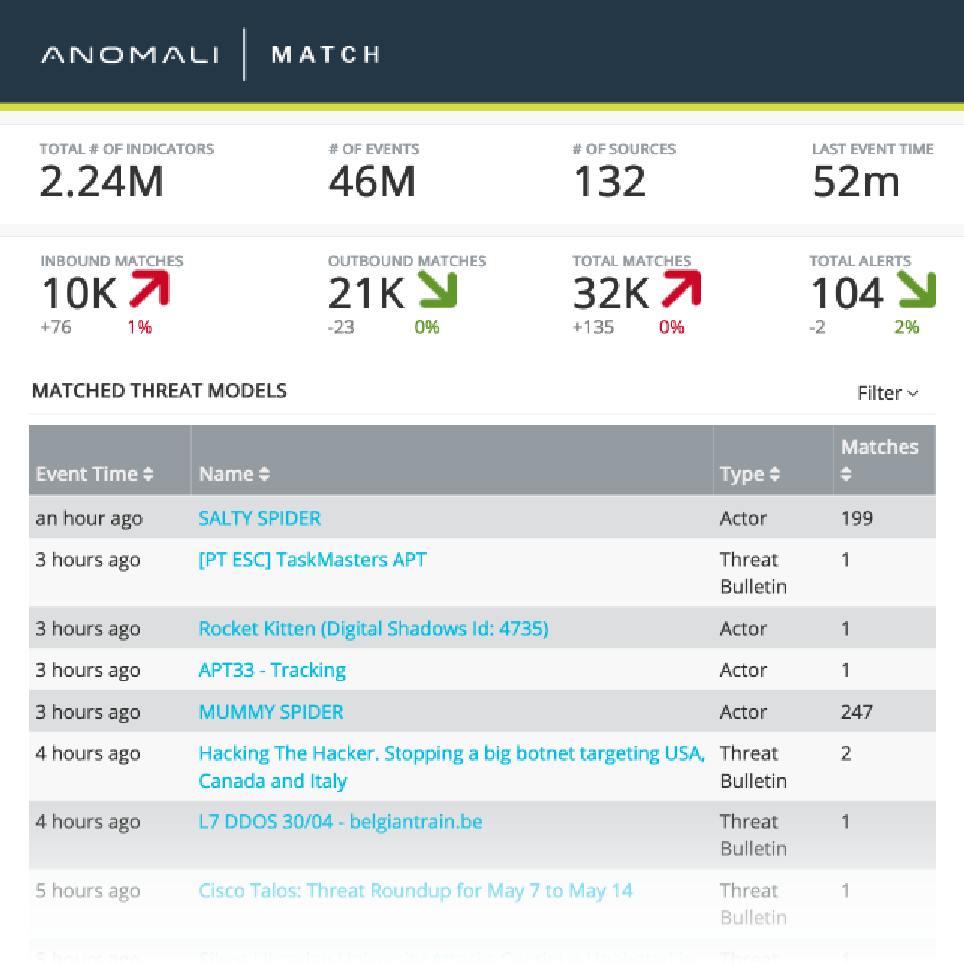
Match uses big data analytics to capture current and historical event logs, asset data, and active threat intelligence to transform billions of alerts into one decisive response. Match collects security telemetry from across your organization – SIEM, EDR, messaging, and network – and integrates layered threat detection to pinpoint relevant threats and provide analysts with the actionable intelligence required to investigate the root cause or the precision confirmation of an attack to immediately respond.
- Gain visibility into 5+ years of security telemetry, millions of IOCs, and asset and vulnerability scan data
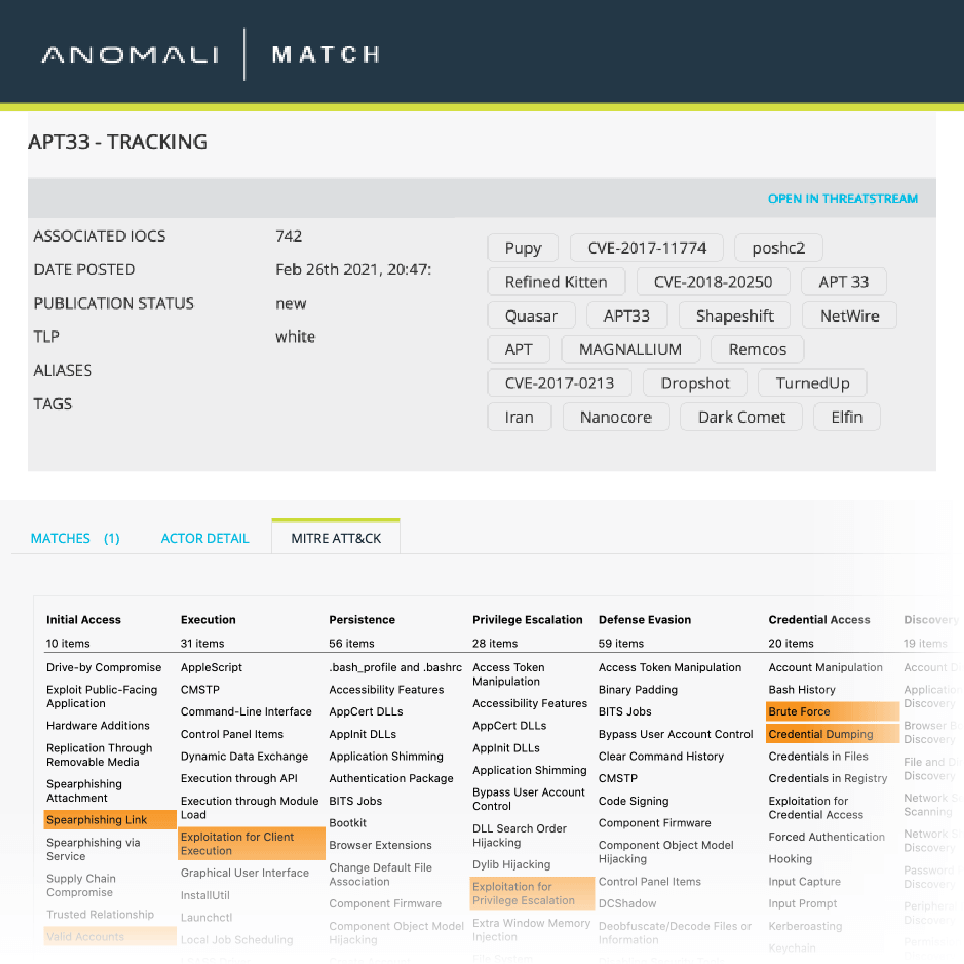
- Integrated layered threat detection, including Sandbox detonation, Domain Generation Algorithm, and Indicator Matching correlation
- Curated high fidelity global intelligence with local telemetry at an unprecedented scale
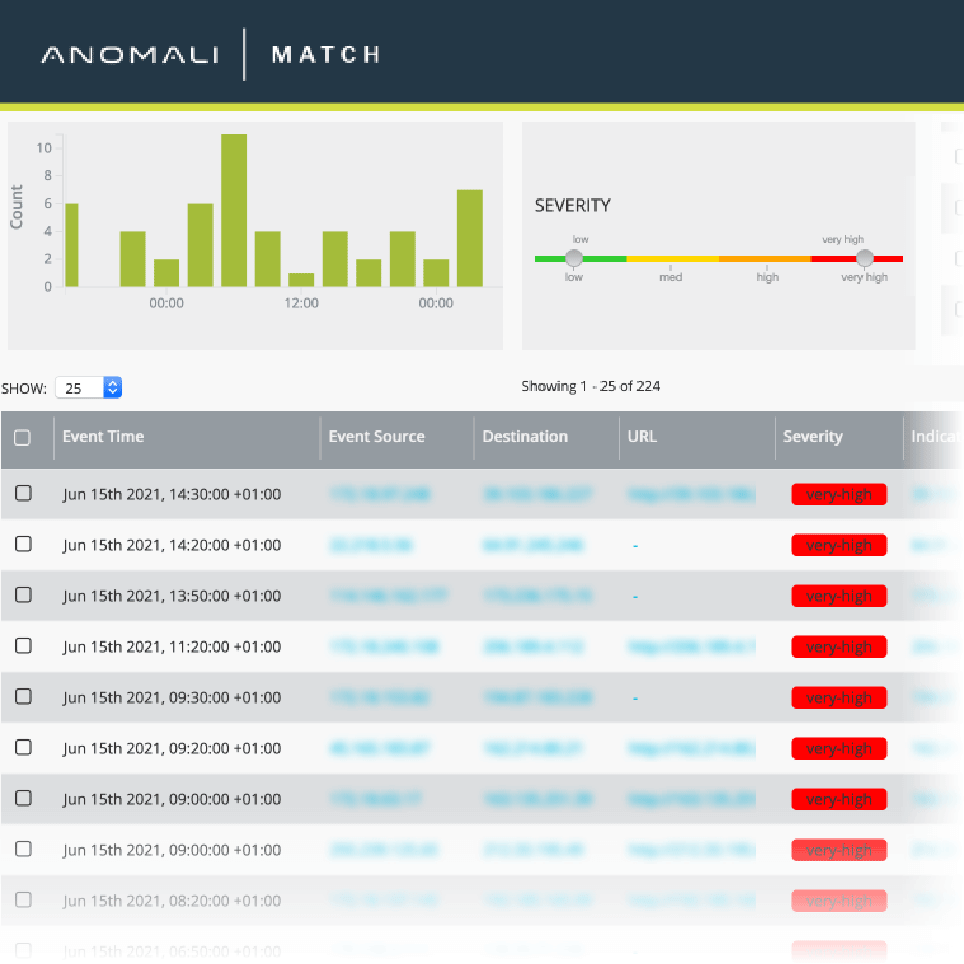
- Enriched alerts with event, asset, indicator, and threat model context, all linked to the underlying raw logs